Multi-pattern Signature Matching for Hardware
Network Intrusion Detection Systems
Haoyu Song,John W.Lockwood {hs1,lockwood }@https://www.doczj.com/doc/9315698530.html,
Department of Computer Science and Engineering Washington University in St.Louis,USA,63130
Abstract —Network Intrusion Detection System (NIDS)per-forms deep inspections on the packet payload to identify,deter and contain the malicious attacks over the Internet.It needs to perform exact matching on multi-pattern signatures in real time.In this paper we introduce an ef?cient data structure called Extended Bloom Filter (EBF)and the corresponding algorithm to perform the multi-pattern signature matching.We also present a technique to support long signature matching so that we need only to maintain a limited number of supported signature lengths for the EBFs.We show that at reasonable hardware cost we can achieve very fast and almost time-deterministic exact matching for thousands of signatures.The architecture takes the advantages of embedded multi-port memories in FPGAs and can be used to build a full-featured hardware-based NIDS.
I.I NTRODUCTION
Some content strings of Internet packet payload,also known as “signatures,”imply network intrusion attempts.Signature-based Network Intrusion Detection System (NIDS)collects these signatures and scans the payload of the Internet packets for them in order to identify,deter and contain such malicious behaviors.A scalable and fast solution is needed to accom-modate the largest signature set today and to sustain the real time processing of the high-speed network.
Bloom Filter [4]is an ef?cient data structure enabling fast membership query with tunable false positive rate.Dharma-purikar et al have designed a multi-pattern signature-matching scheme using Bloom Filters [6].On the scan process,when-ever the front-end Bloom Filter reports a possible match,the string is extracted and used to probe another independent hash table to decide the ?nal match.There are two drawbacks in this scheme.Firstly,the extra lookups in the hash table might become the performance bottleneck due to the hash collisions.Secondly,there are many different signature lengths and the signature distribution on length is unbalanced,so to assign each length a Bloom Filter is inef?cient in memory usage.We ?nd that the scheme does not effectively use the information revealed by the Bloom Filters and there is little consideration about the string load balancing among different Bloom Filters.To overcome these drawbacks,we propose an extension of the Bloom Filter data structure and a new lookup algorithm named Extended Bloom Filter (EBF).It is scalable and suitable for fast incremental updates.The hardware-based EBF is an alternative of the multi-pattern signature-matching problem and outperforms the software-based algorithms.
In this paper,we review the related work in Section II and then discuss our data structure and algorithms in Section III.A theoretical analysis and simulations follow in Section IV and V.Some improvements are presented in Section VI to further reduce the memory usage and boost the performance.The scheme to reduce the number of EBFs is introduced in VII.We brie?y talk about the hardware NIDS implementation in Section VIII and conclude our contribution in Section IX.
II.R ELATED W ORK
Given a packet payload T of length n and a set of m signa-tures S [1]...S [m ]of variable length for intrusion detection,the signature-matching problem is to determine any exact match of signature S [i ]and a substring of T .In NIDS,signature matching is a crucial component and decides the overall system performance.An analysis shows that in Snort,an open-source software-based NIDS,the signature matching alone consumes 30%to 80%of the CPU time [9].While the network bandwidth and the size of the signature set keep growing,to perform real time detection is still far from realistic.
Boyer-Moore is the best-known algorithm for single string matching and is actually adopted for the implementation of the Snort.Fisk extended the Boyer-Moore algorithm to support set-wise string matching [8].Coit does similar work in [5].Aho-Corasick [2]is a ?nite state automaton supporting multi-pattern string matching.The major drawback is its excessive memory consuming.A modi?ed algorithm of Aho-Corasick due to Tuck [14]reduces the amount of memory and improves its performance.Wu-Manber [15]uses a hash table plus the bad character heuristics to accelerate the searching speed.All these algorithms are developed mainly for software imple-mentation.Analysis and experiments show no such algorithm is fast enough for real-time string matching in high-speed network.Thus,a hardware-assisted or pure hardware solution is becoming more and more attractive.
Sidhu [12]implemented Nondeterministic Finite Automaton (NFA)in hardware and later Moscola [10]implemented De-terministic Finite Automaton (DFA)in hardware to perform regular expression matching.While the match speed is fast,they both suffer the scalability problem:Too many states consume too many hardware resources.Dharmapurikar then proposed to use Bloom Filters to do the deep packet inspection [6].Attig implemented a prototype of this scheme [3].Our paper proposes signi?cant improvement to this work and
0-7803-9415-1/05/$20.00 (C) 2005 IEEE
Multi-pattern Signature Matching for Hardware Network Intrusion Detection Systems, by Haoyu Song and John W. Lockwood, IEEE Globecom 2005, St. Louis, MO, Nov. 28, 2005, pp. CN-02-3.
addresses more problems in a real hardware based NIDS im-plementation.Recently,Yu proposed a TCAM-based scheme for multi-pattern matching[16].Despite the widely criticized inef?ciency of TCAM device,the long string matching support involves multiple tables.
III.EBF D ATA S TRUCTURE AND A
LGORITHM
Fig.1.EBF Data Structure
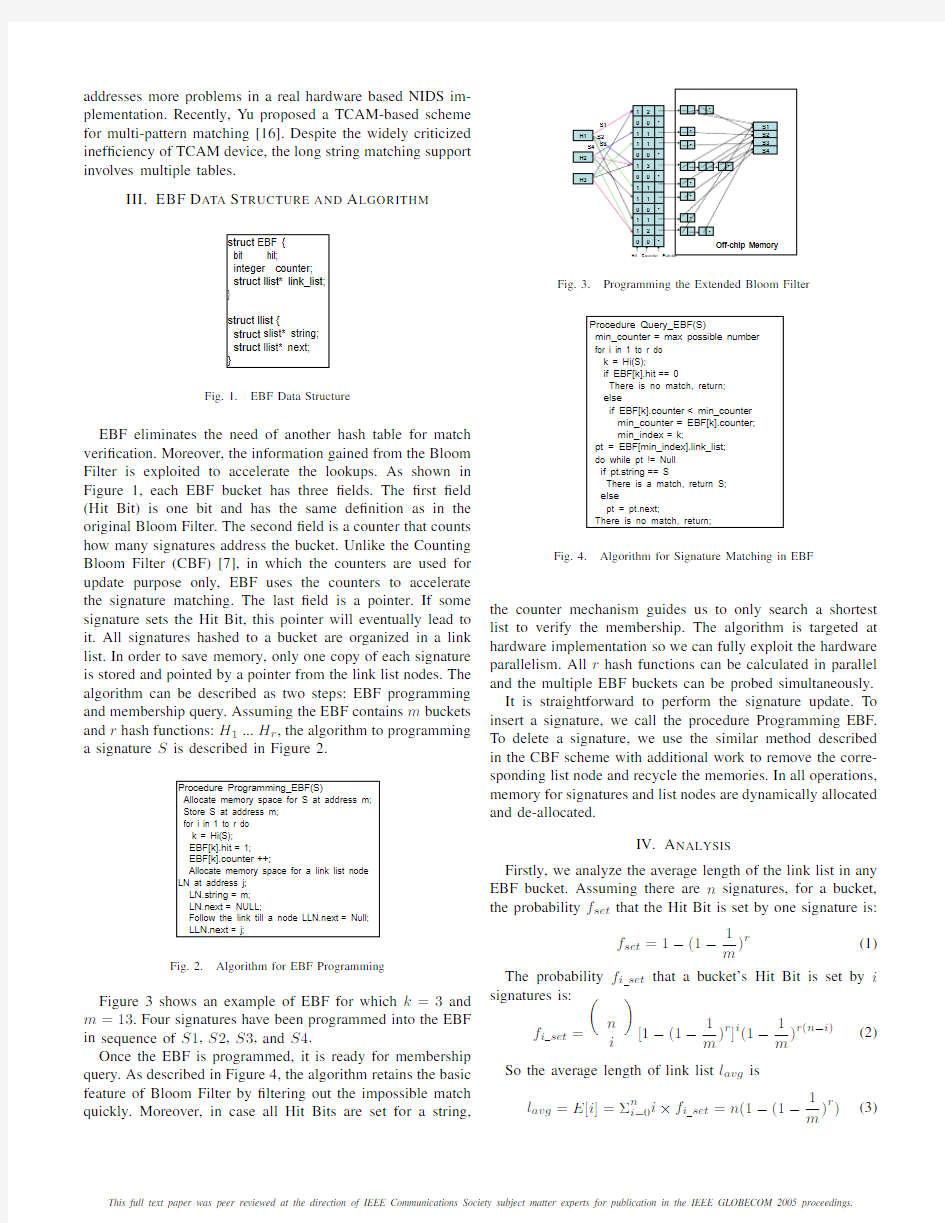
EBF eliminates the need of another hash table for match veri?cation.Moreover,the information gained from the Bloom Filter is exploited to accelerate the lookups.As shown in Figure1,each EBF bucket has three?elds.The?rst?eld (Hit Bit)is one bit and has the same de?nition as in the original Bloom Filter.The second?eld is a counter that counts how many signatures address the bucket.Unlike the Counting Bloom Filter(CBF)[7],in which the counters are used for update purpose only,EBF uses the counters to accelerate the signature matching.The last?eld is a pointer.If some signature sets the Hit Bit,this pointer will eventually lead to it.All signatures hashed to a bucket are organized in a link list.In order to save memory,only one copy of each signature is stored and pointed by a pointer from the link list nodes.The algorithm can be described as two steps:EBF programming and membership query.Assuming the EBF contains m buckets and r hash functions:H1...H r,the algorithm to programming a signature S is described in Figure
2.
Fig.2.Algorithm for EBF Programming
Figure3shows an example of EBF for which k=3and m=13.Four signatures have been programmed into the EBF in sequence of S1,S2,S3,and S4.
Once the EBF is programmed,it is ready for membership query.As described in Figure4,the algorithm retains the basic feature of Bloom Filter by?ltering out the impossible match quickly.Moreover,in case all Hit Bits are set for a string,
Fig.3.Programming the Extended Bloom Filter
Fig.4.Algorithm for Signature Matching in EBF
the counter mechanism guides us to only search a shortest list to verify the membership.The algorithm is targeted at hardware implementation so we can fully exploit the hardware parallelism.All r hash functions can be calculated in parallel and the multiple EBF buckets can be probed simultaneously. It is straightforward to perform the signature update.To insert a signature,we call the procedure Programming EBF. To delete a signature,we use the similar method described in the CBF scheme with additional work to remove the corre-sponding list node and recycle the memories.In all operations, memory for signatures and list nodes are dynamically allocated and de-allocated.
IV.A NALYSIS
Firstly,we analyze the average length of the link list in any EBF bucket.Assuming there are n signatures,for a bucket, the probability f set that the Hit Bit is set by one signature is:
f set=1?(1?
1
m
)r(1) The probability f i set that a bucket’s Hit Bit is set by i signatures is:
f i set=
n
i
[1?(1?
1
m
)r]i(1?
1
m
)r(n?i)(2) So the average length of link list l avg is
l avg=E[i]=Σn i=0i×f i set=n(1?(1?
1
m
)r)(3)
For the Bloom Filter,when the false positive probability is minimized with respect to r,we get the relation
r=(m/n)ln2(4) Based on these analysis,the approximation of link list length as:
l avg=n(1?(1?1
m
)(m/n)ln2)≈ln2≈0.7(5)
Under the same conditions,the probability for a bucket to be
empty is roughly0.5.This implies that half of the total buckets
are never hit by any member https://www.doczj.com/doc/9315698530.html,ing same parameters
as in[3]’s Bloom Filter implementation,the false positive rate
is as low as0.00097and the average link list length is only 0.4.This result shows that the link list is typically very short. Theoretically,if the r buckets are randomly selected from
all the buckets with non-zero counter value,we would like to
know the expected shortest link list.Assuming the percentage
of buckets with a counter value of i over all the buckets with
non-zero counter value is p i.P(j)is the probability that the
smallest counter value is j among the r randomly selected
buckets.Therefore,we get the equation:
P(1)=1?P(>1)=1?(1?p1)r(6) and when j>1
P(j)=1?P(
=(1?Σj?1
k=1
p k)r?(1?Σj k=1p k)r(7) The expected value of j is
E[j]=Σ∞j=1j×P(j)=1+Σ∞s=1(1?Σs t=1p t)r(8) We know that in the optimal case,half of the bucket have a zero value counter,so we have the relation:
p i=2×f i set(9) Using the optimal EBF parameters,P(1)is greater than 0.99and E[j]is slightly larger than one.This shows in most cases actually,only the link lists with length one need to be checked if none of the r hashed counters is zero.Note that the analysis is not very strict and only re?ect the approximate results.We use simulations as backup in the following section.
V.S IMULATION
Simulation results support our theoretical analysis.We use
the same parameter con?gurations as in[3]:1419signatures
are programmed by10hash functions into a20K-bucket EBF.
In the worst and extremely rare cases,at most two memory
accesses are needed.In case that the signatures are all2-byte
long,we test all the65535possible strings,only seven of
them need two memory accesses and others need only one,
even though the link list lengths range from two to?ve.The
longer signature cases exhibit even better performance.
We also did some experiments based on the different com-
binations of the number of hash functions and EBF buckets
Fig.5.Simulation I
as shown in Figure5.We ran a million queries that cover all the programmed signatures.The“Max Length”curve indicates the length of the longest link list in EBF.As more signatures are programmed into EBF,the maximum length of link list grows.Fortunately,we do not need to traverse the longest list.The“Max Hit Length”curve shows the longest list we need to traverse in order to?nd the
matching in any query. By decreasing the number of hash functions or increasing the number of buckets,we can effectively lower this number. However,using less hash functions may increase the false positive rate and using more EBF buckets will increase the resource consumption.Finally,the“Avg Hit Length”curve shows the average length of the list we traverse during the simulation.This number is typically less than two.For the Snort signatures,we have shown for any speci?c length, there are about or much fewer than100distinct signatures. In this case,our experiments indicates only one list node check is needed.By?ne-tuning the parameters,we can support more than1000signatures with tolerable number of memory accesses.
To test the effect on Snort rule set,for each signature length, we only program200distinct signatures in EBF.This leaves spacious room for future update.By varying the number of EBF buckets and the number of hash functions,we see how the number of false positive match and average number of link list accesses change as shown in Figure6.
Fig.6.Simulation II
VI.EBF O PTIMIZATIONS
The EBF is stored in on-chip multi-port SRAM that enables parallel access in one clock cycle.Beside the Hit Bit,we budget4bits for the counter that supports link list length up to 15.We leave11bits to the pointer?eld that distinguish up to 2K signatures.Thus,each bucket is only2-byte.With a40K-byte on-chip SRAM,we could support2K any length signature matching.Now we introduce several optimizations to further improve the storage ef?ciency and lookup performance. Max-Min Threshold:After all signatures are programmed, the minimum link list length for each signature S i is min(S i).
A value
B is maintained along with EBF,where B= max{min(S i)...,?S i}.The usage of B is straightforward: whenever the Bloom Filter reports a match but the queried minimum counter value is greater than B,we know for sure this is a false positive so no link list access is needed.This heuristics comes form the observation that given the small false positive rate,min(S i)tends to be small.When20K buckets,10hash functions and2000signatures are used, simulation shows B=1and for1million test inputs there are 114false positive matches with shortest link list longer than 1.This simple improvement eliminates most of the expensive and unnecessary memory accesses.
Compressed Counter:In previous description,we separate the“Hit bit”and Counter in EBF.Actually,a non-zero counter implies some signatures hit the bucket so the“Hit bit”is redundant.A more aggressive counter scheme is used in EBF implementation.Each on-chip EBF bucket only contains k bits for a saturated counter,where k= log(B+1) +1. The pointer?eld is maintained in a table located in off-chip memories.In practical EBF con?gurations where B is often less than two,two bits are enough to represent the counter and differentiate all useful scenarios,where saturated value“11”means the bucket is hit by three or more signatures.With this optimization,same design mentioned at the beginning of this section can be achieved by using only40K-bit on-chip memories.Note that this saturated counter scheme loses the ability to track the real number of signatures in a list. Shared Link List Nodes:In EBF,up to r link list nodes are allocated for one signature since r hash functions are used. Assuming each link list node is4-byte and each signature is 32-byte,to support2000signatures we need roughly144K-byte memory.Considering in Snort rule set there are almost 50distinct signature lengths,we have the scalability issue to support multiple EBFs.By slightly modifying our algorithm, we can greatly eliminate the data structure redundancy.Ideally, if we always perform a deterministic lookup to the off-chip memory,we need only store a single list node for a signature. However,we want to support the fast incremental updates, and the simple and uni?ed control operations to EBF,so we introduce a scheme that is not optimal but still signi?cant in memory reducing.
When we program a signature in EBF,we need update r EBF buckets.We always insert the signature at the head of the list.For all the buckets that have not been set by any other signature,we only allocate one list node shared by these buckets.Since we already know that most of lists in EBF only include one node,this scheme can signi?cantly reduce the memory consumption compared with the original one. The formal description of the improved algorithm is shown in Figure
7
Fig.7.Improved EBF Programming Algorithm
In Figure8,we use10hash functions and20K EBF buckets to test our improved algorithm.Simulation shows63%to90% memory saving and the saving is more signi?cant when the number of signatures is smaller.However,the absolute saving becomes bigger and bigger when the number of signatures increases.
Fig.8.Memory Saving with Improved Algorithm
Other optimization is also possible.Since we only store each signature once by using exogenous link lists,this doubles the number of memory accesses to retrieve a signature.To improve the lookup performance,we can save a short hash digest in each link list node to avoid the unnecessary comparison with the long signature itself by comparing the hash digest?rst.
VII.L ONG S IGNATURE M ATCHING
The signature lengths distribute in a large range from a few bytes to hundreds.In a parallel computing environment,it is infeasible to maintain an EBF for each signature length. Based on the system resource availability,we set a threshold t.Any signature longer than t should be segmented into a set of substrings with length of t except the last substring that the
length is possible shorter than t.Two more bits are needed to store along with each substring in off-chip memory.One bit indicates if this substring is a partial match,the other bit indicates if this partial match substring is the?rst segment.We also maintain two other tables.One is the Partial Match Table (PMT)with t×t bytes.One extra bit for each entry indicates if this entry is valid.The other table is the Concatenate Veri?cation Table(CVT)that stores all the combinations of two segments that form the substrings of the signatures.One extra bit indicates if this is the last two segments.CVT could be implemented using hash table or CAM.
From the start of payload scan,a pointer p is calculates as (#of bytes scanned)%t.Table I shows the algorithm for long signature matching.
TABLE I
L ONG S IGNATURE M ATCHING A LGORITHM
if a string is partial and the?rst segment
register it in entry p
else if a string is partial but not the?rst segment
if the PMT entry p is valid
concatenate this string with content in entry p
lookup the CVT
if found in CVT
if indicate this is the last block
report match
else
replace the old entry in PMT with this string
else
drop it
invalidate the entry p
else
drop it
For Snort rule set,if we set t=24,then PMT is only 576bytes and the CVT needs to store only about20048-byte substrings.We need only maintain less than24EBFs instead of more than50.
VIII.I MPLEMENTATION
Network Intrusion Detection Systems need to inspect the packets based on both the header and payload.A hardware-based NIDS,taking the advantages of the stat-of-art FPGA technology,is proposed to implement the Snort rule matching. Figure9illustrates the high-level overview of the system. The layered protocol wrappers are used to handle the TCP/IP header and maintain the?ow state[11]and the module of packet header classi?cation is used to inspect the packet header and help to match the full rules[13].We implement our data structure and lookup algorithm in string matching module to identify the signatures.
An FPGA chip can contain more than10-Mbits SRAMs, con?gured in different depth and width[1].We implement the front-end EBF data structure on-chip by taking advantage of these?exible multi-port SRAMs.
The link lists and signatures are stored in off-chip memory. The memory management logic dynamically allocates the memory for them.The operation takes several clock cycles. This extra complexity only happens when we initialize or
Fig.9.FPGA-based NIDS
update the signatures in EBF.As we know,the database updating is relatively infrequent compared with the signature matching task,so this is not a serious concern.
IX.C ONCLUSION
In this paper,we present a new data structure that extends the classical Bloom Filter.We propose the corresponding al-gorithms for hardware-based multi-pattern signature matching. We also present a scheme to support long signature matching. We demonstrate that our EBF algorithm is highly ef?cient in terms of both throughput and memory storage.We integrate this algorithm into a full-featured hardware-based NIDS.We believe this is a key step towards building a real time NIDS, which is capable of actively monitoring and?ltering all pass-through traf?c even in a high-speed network.
R EFERENCES
[1]Xilinx Inc.Virtex-II Pro and Virtex-II Pro X Platform FPGAs:Complete
Data Sheet,2004.
[2] A.Aho and M.J.Corasick.Ef?cient string matching:An aid to
bibliographic https://www.doczj.com/doc/9315698530.html,munications of the ACM,June1975.
[3]M.Attig,S.Dharmapurikar,and J.Lockwood.Implementation of bloom
?lters for string matching.In FCCM,2004.
[4] B.Bloom.Space/time trade-offs in hash coding with allowable errors.
Communications of the ACM,July1970.
[5] C.J.Coit,S.Staniford,and J.McAlerney.Towards faster pattern
matching for intrusion detection or exceeding the speed of snort.In DISCEX II,2001.
[6]S.Dharmapurikar,P.Krishnamurthy,T.Sproull,and J.W.Lockwood.
Deep Packet Inspection Using Parallel Bloom Filters.In HotI,2003.
[7]L.Fan,P.Cao,J.Almeida,and A.Broder.Summary cache:a scalable
wide-area web cache sharing protocol.IEEE/ACM Transactions on Networking,Mar.2000.
[8]M.Fisk and G.Varghese.Applying fast string matching to intrusion
detection,2004.
[9] E.P.Markatos,S.Antonatos,M.Polychronakis,and K.G.Anagnos-
takis.Exclusion-based signature matching for intrusion detection.In CCN,2002.
[10]J.Moscola,J.Lockwood,R.P.Loui,and M.Pachos.Implementation
of a content-scanning module for an Internet?rewall.In FCCM,2003.
[11] D.V.Schuehler,J.Moscola,and J.W.Lockwood.Architecture for a
Hardware Based,TCP/IP Content Scanning System.In HotI,2003. [12]R.Sidhu and V.K.Prasanna.Fast regualr expression matching using
fpgas.In FCCM,2001.
[13]H.Song and J.Lockwood.Ef?cient Packet Classi?cation for Network
Intrusion Detection Using FPGA.In ACM FPGA,2005.
[14]N.Tuck,T.Sherwood,B.Calder,and G.Varghese.Deterministic
memory-ef?cient string matching algorithms for intrusion detection.In IEEE Infocom,2004.
[15]S.Wu and U.Manber.A fast algorithm for multi-pattern searching.
Technical Report TR-94-17,1994.
[16] F.Yu,R.Katz,and https://www.doczj.com/doc/9315698530.html,kshman.Gigabit Rate Packet Pattern-Matching
Using TCAM.
第12讲:等离子体(IV)——局域表面等离子体 课本: S.Maier,Plasmonics:Fundamentals and Applications ,Chap.5 董国艳 中国科学院大学材料科学与光电技术学院 纳米光学 (Nano-Optics) 研究生课程 2 课前思考: ?? 金子小颗粒(nm-size)是什么颜色的?为什么它们会成像不同的颜色?
3 1.金属纳米粒子的局域表面等离子体(Localized surface plasmons LSPs ) ????偶极辐射的回顾 LSP 的纳米粒子(准静态近似) LSPR 的大小和形状依赖性(Mie 理论)LSP 的纳米棒(Gans 理论) 3. LSP 粒子之间的耦合 4.LSP 的复杂的纳米结构–球壳 5. 体积等离子体,SPP 和LSP 的比较 本讲内容 2. LSP 的共振条件 ? LSP同SPP 的差异 ? 金属纳米粒子的色彩效果? 各种金属纳米粒子 4 1.金属纳米粒子的LSP ?SPPs :在金属-电介质延展界面上的SP 传输(光子耦合为SP).+ -+ k ?LSPs (localized surface plasmons 局域表面等离子体):在金属纳米粒子/纳米空腔的封闭表面上不传播的SPs ?LSP 的激发将影响透过纳米粒子的光的消光比(= 吸收+散射) →色彩效果 extinction:消光比,absorption:吸收,scattering:散射 LSP 被约束在粒子上
5 金属粒子的色彩效应 过去: 不同的形状&大小→不同的色彩 Au colloids in water (M.Faraday ~1856) Lycurgus Cup 教堂窗户上的彩色玻璃 今天(出于同样原理): colloid:胶体,stained glass:彩色玻璃 聚焦和传导光到纳米粒子上 金属纳米粒子胶体 6 Nano-shell Nano-prism Nano-pentagon Nano-rod Various metal nanoparticles Simplest to analyze Nano-sphere shell:空壳,rod:棒,sphere:球,pentagon:五边形
四种翻译方法 1.直译和意译 所谓直译,就是在译文语言条件许可时,在译文中既保持原文的内容,又保持原文的形式——特别指保持原文的比喻、形象和民族、地方色彩等。 每一个民族语言都有它自己的词汇、句法结构和表达方法。当原文的思想内容与译文的表达形式有矛盾不宜采用直译法处理时,就应采用意译法。意译要求译文能正确表达原文的内容,但可以不拘泥与原文的形式。(张培基) 应当指出,在再能确切的表达原作思想内容和不违背译文语言规范的条件下,直译有其可取之处,一方面有助于保存原著的格调,另一方面可以进新鲜的表达方法。 Literal translation refers to an adequate representation of the original. When the original coincides or almost tallies with the Chinese language in the sequence of vocabulary, in grammatical structure and rhetorical device, literal translation must be used. Free translation is also called liberal translation, which does not adhere strictly to the form or word order of the original.(郭著章) 直译法是指在不违背英语文化的前提下,在英译文中完全保留汉语词语的指称意义,求得内容和形式相符的方法。
解析雅思阅读信息配对题 关于雅思阅读当中的配对题,很多学生和老师都已经习惯了称它为matching题。但matching的范畴太过于宽泛,如果刻意细分的话,我们还可以把它分为单词配描述,句子完成题和段落信息配对题三个大类。针对句子完成题(题干往往为complete each sentence with the correct ending)和段落信息配对题(题干往往为which paragraph contains the following information),我将以后另开专题来讲解,本次将重点讲解最传统的配对题型(单词配描述),并根据雅思阅读题干部分将其继续细分为match题(match each XX with the correct statement)和classify题(classify the following features)。 首先强调一下配对题的基本功:定位能力+词汇量积累 我们分别来解释一下。定位,就是拿着给定的主语去文章当中去找到位置。这些主语往往是专有名词,首字母都会大写。这一个步骤看起来很容易,也不需要任何语言能力和技巧,我们经常开玩笑说就算这是一篇法语的文章,这一步也能很快搞掂。但在大班课堂的练习中,我们会发现,有很多同学定位单词耗费时间太多,往往三四个单词就要找两三分钟,无形中给自己增添了很多时间紧迫的压力。而这种办法的唯一破解,就是拿着一些练习题做专项训练,而唯一的技巧在于,match 类(非classify类)的定位词出题顺序与文章中原词的出现顺序是一致的,一项找不到,我们就用夹击法,把前后项都找到,当中的就好找了。 那么为什么强调词汇量的积累呢?因为到了我们配对题的关键破题点,会发现想在原文中找到与选项中一摸一样的单词或句子并不容易,往往会用到近义词转述,比如unable会变成at loss,lay stress on会变成emphasize。这些单词看起来很简单,但能不能意识到他们之间的近义词关系,需要课下多进行“词以类记”的单词强化记忆,单词不求难,但求精准和举一反三。 下面我们先说说match一类题型的做题步骤。 以雅思剑桥真题集5,第91页的题为例: Look at the following people and the list of statements below. Match each person with the correct statement. Write the correct letter A-H in boxes 14-17 on your answer
雅思A类阅读考题回顾(第二季度)
Passage 2 资料考证来源于维基百科 After repairs, she plied for several years as a passe nger liner between Britain and America, before being converted to a cable-laying ship and la ying the first lasting” Brunel worked for several years as assistant engineer on the project to create a tunnel unde r London's River Thames 题目配对 tunnel under river Thames -- which Brune was not responsibl e for it Though ultimately unsuccessful, another of Brunel's interesting use of technical innovat ions was the atmospheric railway 配对建成不久就停止运营那项吧 Great Eastern was designed to cruise non-stop from London to Sydney and back (since engi neers of the time misunderstood that Australia had no coal reserves), and she remained the l argest ship built until the turn of the century. Like many of Brunel's ambitious projects, t he ship soon ran over budget and behind schedule in the face of a series of technical probl ems.great eastern 配对建设推迟了很对次和财务上不成功我配了两个
表面等离子体 (surface plasmons,SPs)是一种电磁表面波,它在表面处场强最大,在垂直于界面方向是指数衰减场,它能够被电子也能被光波激发。表面等离子体是目前纳米光电子学科的一个重要的研究方向,它受到了包括物理学家,化学家材料学家,生物学家等多个领域人士的极大的关注。随着纳米技术的发展,表面等离子体被广泛研究用于光子学,数据存储,显微镜,太阳能电池和生物传感等方面。 表面等离子体 表面等离子体 - 科学历史 1902年,R. W. Wood在光学实验中首次发现了表面等离激元共振现象。1941年,U. J. Fano等人根据金属和空气界面上表面电磁波的激发解释了这一现象。R. H. Ritchie注意到,当高能电子通过金属薄膜时,不仅在等离激元频率处有能量损失,在更低频率处也有能量损失峰,并认为这与金属薄膜的界面有关。1959年,C. J. Powell和J. B. Swan通过实验证实了R. H. Ritchie的理论。1960年,E. A. Stren和R. A. Farrel研究了此种模式产生共振的条件并首次提出了表面等离激元(Surface Plasmon,SP)的概念。在纳米技术成熟之后,表面等离子体受到了人们极大的关注,成为目前研究的热点。它已经被应用于包括生物化学传感,光电子集成器件多个领域。 表面等离子体 - 基本原理
表面等离子体场分布特性 表面等离子体(Surface Plasmons,SPs)是指在金属表面存在的自由振动的电子与光子相互作用产生的沿着金属表面传播的电子疏密波。其产生的物理原理如下:如作图所示,在两种半无限大、各项同性介质构成的界面,介质的介电常数是正的实数,金属的介电常数是实部为负的复数。根据maxwell方程,结合边界条件和材料的特性,可以计算得出表面等离子体的场分布和色散特性。 一般来说,表面等离子体波的场分布具有以下特性: 1.其场分布在沿着界面方向是高度局域的,是一个消逝波,且在金属中场分布比在介质中分布更集中,一般分布深度与波长量级相同。 2.在平行于表面的方向,场是可以传播的,但是由于金属的损耗存在,所以在传播的过程中会有衰减存在,传播距离有限。 3.表面等离激元的色散曲线在自然光的右侧,在相同频率的情况下,其波矢量比光波矢量要大。 表面等离子体 - 激发方式 表面等离子体 由于在一般情况下,表面等离子体波的波矢量大于光波的波矢量,所以不可能直接用光波激发出表面等离子体波。为为了激励表面等离子体波,需要引入一些特殊的结构达到波矢匹配,常用的结构有以下几种: 1.采用棱镜耦合的方式:棱镜耦合的方式包括两种:一种是Kretschmann结构:金属薄膜直接镀在棱镜面上,入射光在金属-棱镜界面处会发生全反射,全反射的消逝波可能实现与表面等离子体波的波矢量匹配,光的能量便能有效的传递给表面等离子体,从而激发出表面等离子体波。这是目前广泛用于表面等离子体的科研与生产的一种结构。另一种是Otto结构:具有高折射率的棱镜和金属之间
高一英语翻译技巧和方法完整版及练习题及解析 一、高中英语翻译 1.高中英语翻译题:Translation: Translate the following sentences into English, using the words given in the brackets. 1.究竟是什么激发小王学习电子工程的积极性?(motivate) 2.网上支付方便了客户,但是牺牲了他们的隐私。(at the cost of) 3.让我的父母非常满意的是,从这个公寓的餐厅可以俯视街对面的世纪公园,从起居室也可以。(so) 4.博物馆疏于管理,展品积灰,门厅冷落,急需改善。(whose) 【答案】 1.What on earth has motivated Xiao Wang’s enthusiasm/ initiative to major in electronic engineering? 2.Online payment brings convenience to consumers at the cost of their privacy. 3.To my parents’ satisfaction, the dining room of this apartment overlooks the Century Park opposite the street and so it is with the sitting room. 或者What makes my parents really satisfy is that they can see the Century Park from the dining room of this apartment, so can they from the living room. 4.This museum is not well managed, whose exhibits are covered with dust, and there are few visitors, so everything is badly in need of improvement. 或The museum whose management is reckless, whose exhibits are piled with dust and whose lobby is deserted, requires immediate improvement. 【解析】 1.motivate sb to do sth 激发某人做某事,on earth究竟,major in 以…为专业,enthusiasm/ initiative热情/积极性,故翻译为What on earth has motivated Xiao Wang’s enthusiasm/ initiative to major in electronic engineering? 2.online payment网上支付,brings convenience to给…带来方便,at the cost of以…为代价,privacy隐私,故翻译为Online payment brings convenience to consumers at the cost of their privacy. 3.To my parents’ satisfaction令我父母满意的是,后者也那样so it is with。也可以用主语从句What makes my parents really satisfy 表语从句thatthey can see the Century Park from the dining room of this apartment。overlooks俯视,opposite the street街对面,living room 起居室。故翻译为To my parents’ satisfaction, the dining room of this apartment overlooks the Century Park opposite the street and so it is with the sitting room.或者What makes my parents really satisfy is that they can see the Century Park from the dining room of this apartment, so can they from the living room. 4.not well managed/ management is reckless疏于管理,be covered with dust/ be piled with dust被灰尘覆盖,few visitors游客稀少,be badly in need of improvement/ requires immediate improvement亟需改善。故翻译为his museum is not well managed, whose exhibits
“黑技巧”教你搞定雅思阅读最难题型段落matching题 作者简介: 詹逸雄,环球雅思阅读女教师一枚,但是因为名字很有mafia老大的气质,很多同事 和学生会叫我熊哥…听力阅读均9分,硕士就读于UCL英语教育专业。 写在前面的话: 段落matching题,英文名称为which paragraph contains the following information? 问的是题目的内容在文章哪段出现。这种题型,江湖上人称“断子绝孙题”,一听名字 就让烤鸭们虎躯一震,身体某个部位随之一紧,学渣闻风丧胆,学霸也抓耳挠腮。很 多学渣被这个题型虐过几次之后,基本上处于放弃治疗状态,最后纯蒙大法了事。甚 至业界一些老师给出的策略也很佛系:反正你也做不好,留到最后做,能做成咋样就 咋样...段落matching题确实难,但最大的问题是绝大部分烤鸭都没有一个正确的做题方法!!真是让熊哥痛心疾首,今天熊哥就来教大家段落matching题正确的做题方法,再配以一些黑技巧,让大家看到段落matching题感觉so easy,妈妈再也不担心我的 学习! 讲述段落matching题正确的方法前,先诊断一下烤鸭们可能存在的问题: 1.完全凭感觉,在各段乱找乱瞟。这类同学,正确率经常不稳定,好的时候也能 对不少,差的时候基本没有对的,当然差的时候居多。。。这类同学,用上熊 哥正确的方法,正确率和稳定性很容易都提上来!!! 2.题目都读不懂,只能找找哪段出现了题目中的原词,找不到原词的就纯蒙了事。 说句实在话,这类同学建议先背单词,关于单词,熊哥有很多话要说,等我拖 延症痊愈了(怎么可能???),等我拖延症病情缓解了,就好好码字给大家 分享背什么单词,以及背单词的方法。其实,雅思阅读文章有生词很正常,熊 哥能考到9分,但自己的雅思书上也会有零(mì)星(mì)几(má)个(má)的生词,所以熊哥上课从来不带阅读书,一方面是为了装X显示自己对于文章 熟悉,另一方面主要是怕背学生看到我查的生词有(guò)点(yú)多,影响 我的光辉形象(好像并没有任何形象可言...)BUT!BUT!我说的是文章有生
LSPs和PSPs的区别 局域表面等离子体(Localized Surface plasmons, LSPs)和传播型表面等离子体(Propagating surface plasmons. PSPs)同属于表面等离子体(SPs)1。 表面等离子体(SP)是存在于金属与电介质截面的自由电子的集体振荡2。SPR是由于入射激光在特殊波长处局域电磁场增强,物理机制是表面增强拉曼散射(Surface-enhanced Raman scattering, SERS)和尖端增强拉曼散射(Tip-enhanced Raman scattering, TERS)。 入射光的电场分量诱导球形金属粒子的表面等离子体共振的原理分析(即图1的解读)3。 当入射光照射到贵金属(如:金、银,见脚注1、3)时,在纳米颗粒表面形成一种振荡电场,纳米颗粒中的自由传导电子在振荡电场的激发下集体振荡,入射光子频率与金属纳米颗粒的自由电子云的集体振动频率相等(入射光波长一定)时,发生局域表面等离子体共振(LSPR)。亦可解释为入射光在球形颗粒表面产生电场分量,电子的共谐振荡与激发其的振荡电场频率相同时发生共振,诱导产生LSPR 3。 对于LSPs而言,颗粒内外近场区域的场强会被极大增强,原因是:纳米粒子的尺寸远小于入射光波长,使得电子被束缚在纳米粒子周围局域振荡,导致场强增大。 对于PSPs(部分文章中称为:SPPs4,金属与介质界面上的电子集体激发振荡的传播型表面电磁波),其表面等离子激元(即TM模式)如上图所示。在SPPs 的情况下,沿金属介质界面,等离子体在X和Y方向上传播,在Z方向上衰减, 1等离激元学[M]. 东南大学出版社, 2014. 2 Zhang Z, Xu P, Yang X, et al. Surface plasmon-driven photocatalysis in ambient, aqueous and high-vacuum monitored by SERS and TERS[J]. Journal of Photochemistry & Photobiology C Photochemistry Reviews, 2016, 27:100-112. 3邵先坤, 郝勇敢, 刘同宣,等. 基于表面等离子体共振效应的Ag(Au)/半导体纳米复合光催化剂的研究进展[J]. 化工进展, 2016, 35(1):131-137. 4王五松, 张利伟, 张冶文. 表面等离子波导及应用[J]. 中国光学, 2015(3):329-339.
文言文翻译技巧和方法 一、基本方法:直译和意译文言文翻译的基本方法有直译和意译两种。所谓直译,是指用现代汉语的词对原文进行逐字逐句地对应翻译,做到实词、虚词尽可能文意相对。直译的好处是字字落实;其不足之处是有时译句文意难懂,语言也不够通顺。所谓意译,则是根据语句的意思进行翻译,做到尽量符合原文意思,语句尽可能照顾原文词义。意译有一定的灵活性,文字可增可减,词语的位置可以变化,句式也可以变化。意译的好处是文意连贯,译文符合现代语言的表达习惯,比较通顺、流畅、好懂。其不足之处是有时原文不能字字落实。这两种翻译方法当以直译为主,意译为辅。 二、具体方法:留、删、补、换、调、变。 “留”:就是保留。凡是古今意义相同的词,以及古代的人名、地名、物名、官名、国号、年号、度量衡单位等,翻译时可保留不变。例如:《晏子使楚》中的“楚王”、“晏婴”、“晏子”等不用翻译。 “删”,就是删除。删掉无须译出的文言虚词。例如:“寡人反取病焉”的“焉”是语气助词,可不译,本句的意思就是“我反而自讨没趣。”(《晏子使楚》)又如:“子猷、子敬俱病笃,而子敬先亡”中的“而”是连词,可不译,整句意思是“子猷与子敬都病重,子敬先死去。” “补”,就是增补。(1)变单音词为双音词,如《桃花源记》中“率妻子邑人来此绝境”,“妻子”一词是“妻子、儿女”的意思;(2)补出省略句中的省略成分,如《人琴俱亡》中“语时了不悲”,翻译为:(子猷)说话时候完全不悲伤。 “换”,就是替换。用现代词汇替换古代词汇。如把“吾、余、予”等换成“我”,把“尔、汝”等换成“你”。“调”就是调整。把古汉语倒装句调整为现代汉语句式。例如《人琴俱亡》中“何以都不闻消息”,“何以”是“以何”的倒装,宾语前置句,意思是“为什么”。“变”,就是变通。在忠实于原文的基础上,活译有关文字。“子猷问左右”(人琴俱亡))中的“左右”指的是“手下的人”,“左右对曰”(《晏子使楚》中的“左右”指的是“近臣”。 古文翻译口诀古文翻译,自有顺序,首览全篇,掌握大意;先明主题,搜集信息,由段到句,从句到词,全都理解,连贯一起,对待难句,则需心细,照顾前文,联系后句,
八种雅思阅读题目解题全攻略 本文中,小编将为大家解答有关雅思阅读题目解题的8种攻略。 一、ListofHeadings(标题对应题) 标题对应题在文章后面给出的段落标题一般是10个选项,其中含一到两个段落及其标题的例子。要求对题目中给出的段落,根据其内容找出与其相匹配的段落标题。尽管题目说明中提示一个选项可能会适用多个但中国考区考试中一般一个选项只能用于一个段落。考生应首先在listofHeadings中划去做为例子的heading或headings,以免在根据段落内容在listofHeadings中找出与其相匹配的段落标题时,它(它们)会干扰考试者对其他headings的选择。同时在文章中把做为例子的段落划掉,以免对例子段落进行不必要的精读。 在解答标题对应题目时,考生应对一些可以利用来直接选出答案的词汇加以特别注意。比如:如果一个标题中出现了definition这个词,那么这个标题很有可能就对应文章的第一段,因为在写文章的时候,作者想要引入某一概念时,往往会在第一段就对这个概念下定义。又比如:如果在一个标题中出现了salary,wage等词,那么考生可以到文章中寻找一个含有较多货币符号的段落。当然象这样的窍门还有很多,考生可以在准备雅思学术类阅读考试的过程中不断摸索。对于大部分题目,特别是较难的标题对应题目来说还是要遵循上文所述的基本解题方法来做题的,有时甚至要通读全文. 二、MATCHING(配对题) 这种题型是雅思学术类阅读考试中比较普遍的题型,也是相对而言较为耗费时间和精力的一种题型。配对题主要包含下列几种形式:文章中的重要概念和对这个
概念的阐释配对;学者及其主要观点相配;错误观点(misconception)和反驳错误观点的论据(counterargument)相配;事件和事件的发展过程相配;原因和结果相配;某种标志性事物和其所在的时代相配;新产品和发明家、发明时间等相配。尽管针对不同题目可以有一些解题窍门,但对于大多数配对题来说,答题步骤都是固定而且枯燥的:考生应该首先仔细查看答题指引,了解回答何种问题。查看例句,确定答题方式。弄清那些选项是同义选项,那些选项是反义选项,那些选项是有关数字选项。根据在题目中自己划出的中心词在原文中寻找信息点,注意以大写、斜体、括号和引号方式出现的概念。.对于有关人名与理论、新产品和发明家、时间的配对题,首先要快速找出人名、公司名和时间,然后在附近的上下文中找答案。 三、TURE/FALSE/NOTGIVEN(正误及无关判断题型) 正误及无关判断题是雅思学术类阅读考试当中难度较大的一种题型,在一次考试中出题的数目大概在7-16道题左右.出题方式是给出数个陈述句,让考生根据文章内容判断.如果题目内容与原文内容一致,则选TRUE;如果题目内容与文章内容相抵触,则选FALSE;如果题目内容在原文中并没有提到,则选NOTGIVEN. 在解答TURE/FALSE/NOTGIVEN题型时,考生应该注意到以下几点: 第一这种题型绝对不能够只凭自己的感觉来做题,而一定要回到文章中寻找对应信息。目前中国考区很少出现需要通读全文才能加以判断的 TURE/FALSE/NOTGIVEN题目,即是说考生一定可以在文章中找到一个信息点与文章后的某道题目相对应,另外诸如比喻型题目,虚拟语气题目,复杂时态型题目等
英汉翻译的基本方法和技巧 翻译是信息交流过程中极其复杂的社会心理现象。语言知识是翻译的基础。此外,翻译还涉及到推理、判断、分析和综合等复杂的心理认识过程。翻译的方法和技巧是翻译工作者在长期的实践中根据两种语言的特点总结归纳出来的一般规律。这些规律可以指导我们的翻译实践,使我们能更自觉、更灵活地处理翻译过程中所遇到的各种语言现象。下面就英译汉中的一些方法和技巧结合翻译实例作一概述。 1. 词义的选择 一词多义和一词多类是英汉两种语言都有的一种语言现象。因此,在平日的翻译练习和测试中,我们在弄清原文句子结构后,务必注意选择和确定句中关键词的词类和词义,以保证译文的质量。通常可从以下三个方面来考虑词义选择: 1)根据词在句中的词类来选择词义 例如:Censorship is for the good of society as a whole. Like the law, it contributes to the common good. [译文]:审查是为了整个社会的利益。它像法律一样维护公众利益。 [注释]:本句中like作介词,意为"像……一样"。但like作动词用,则意为"喜欢;想要"。例如:He likes films with happy endings. (他喜欢结局好的电影。)又如:Would you like to leave a message? (你要不要留个话儿?)此外,like还可以作形容词用,意为"相同的",如:Like charges repel; unlike charges attract.(电荷同性相斥,异性相吸。) 2)根据上下文和词在句中的搭配关系选择词义 例1 According to the new s chool of scientists, technology is an overlooked force in expanding the horizons of scientific knowledge. [译文]:新学派的科学家们认为,技术在扩大科学知识范围过程中是一种被忽视的力量。 [注释]:school一词常被误译为"学校",其实,school还有一个词义"学派"。可见,正确选择词义对译文质量有重要影响,而文章的上下文和逻辑联系是翻译中选择词义的重要依据。 例2 Now since the assessment of intelligence is a comparative matter we must be sure that the scale with which we are comparing our subjects provides a "valid" or "fair" comparison. [译文]:既然对智力的评估是比较而言的,那么我们必须确保,在对我们的对象进行比较时,我们所使用的尺度要能提供"有效的"和"公平的"比较。 [注释]:许多人把scale译为"范围",和文章的语篇意思和句子的确切含义大相径庭。
表面等离子体激元研究现状及应用 黄增盛 (桂林电子科技大学信息与通信学院,广西桂林 541004) 摘要:表面等离子体激元(SPPs)是在金属和介质界面传播的一种波动模式,本文主要讨论了的一些基本特性,概述了现在阶段主要的一些激发产生的方式。描述了在集成光通信上的应用,比如基于表面等离子体激元的纳米激光器、新型波导和SPPs耦合器等纳米光子器件。分析了表面等离子体共振(SPR)技术在生物及医疗领域的新应用,并对其在治疗癌症方面的技术原理进行了讨论。介绍了SPPs在新型光源和能源领域的发展和应用情况,最后讨论了SPPs在光存储方面的快速发展。 关键词:表面等离子激元;表面等离子体共振;纳米激光器 The research situation and applications of surface plasmon polaritons Huang Zeng-sheng (School of Information and Communication Engineering, Guilin University of Electronic Technology, Guilin 541004, China) Abstract:Surface plasmon polaritons (SPPs) is in a wave pattern of dielectric and metal interface communication, some basic properties are discussed in this paper, an overview of the main stage generated now some way. Described in the application of integrated optical communication, such as nano lasers, novel waveguide and SPPs coupler base on the surface plasmon. Analysis new technology applies of the surface plasmon resonance (SPR) in biological and medical fields, and the principle of the technique in the treatment of cancer are discussed. Introducing the SPPs development and application in the new field of energy source, and finally discussed the rapid development of SPPs in optical storage. Key words: The surface plasmon polaritons; The surface plasmon resonance; The nano lasers 表面等离子体激元(Surface Plasmon Polaritons, SPPs)是光和金属表面的自由电子相互作用所引起的一种电磁波模式,或者说是在局域金属表面的一种自由电子和光子相互作用形成的混合激发态。它既具有光子学的速度,又具有电子学的尺度,能够在亚波长结构中对光进行约束和操控,被喻为目前最有希望的纳米集成光子器件的信息载体。目前,SPPs 光波导、亚波长孔径的增强透过现象以及光控高速光开关从实验和理论上都得到了广泛的论证。伴随着纳米科技的蓬勃发展,许多有趣的表面等离子体光学器件不断向前推进,在各个领域发挥着越来越重要的作用。 1SPPs 的基本特性 表面等离子体激元是指光子与金属表面的自由电子相互作用而被俘获,外来光子电磁场激发引起金属中电荷密度涨落产生的电磁模式,它沿着金属表面传播,是一种倏逝表面波,满足麦克斯韦方程[2]。
英语翻译技巧 5.拆句法和合并法: 这是两种相对应的翻译方法。拆句法是把一个长而复杂的句子拆译成若干个较短、较简单的句子,通常用于英译汉;合并法是把若干个短句合并成一个长句,一般用于汉译英。汉语强调意合,结构较松散,因此简单句较多;英语强调形合,结构较严密,因此长句较多。所以汉译英时要根据需要注意利用连词、分词、介词、不定式、定语从句、独立结构等把汉语短句连成长句;而英译汉时又常常要在原句的关系代词、关系副词、主谓连接处、并列或转折连接处、后续成分与主体的连接处,以及意群结束处将长句切断,译成汉语分句。这样就可以基本保留英语语序,顺译全句,顺应现代汉语长短句相替、单复句相间的句法修辞原则。如: (1) Increased cooperation with China is in the interests of the United States. 同中国加强合作,符合美国的利益。(在主谓连接处拆译) (2)I wish to thank you for the incomparable hospitalityfor which the Chinese people are justly famous throughout the world. 我要感谢你们无与伦比的盛情款待。中国人民正是以这种热情好客而闻明世界的。(在定语从句前拆译) 6.倒置法: 在汉语中,定语修饰语和状语修饰语往往位于被修饰语之前;在英语中,许多修饰语常常位于被修饰语之后,因此翻译时往往要把原文的语序颠倒过来。倒置法通常用于英译汉, 即对英语长句按照汉语的习惯表达法进行前后调换,按意群或
进行全部倒置,原则是使汉语译句安排符合现代汉语论理叙事的一般逻辑顺序。有时倒置法也用于汉译英。如: (1)At this moment, through the wonder of telecommunications, more people are seeing and hearing what we say than on any other occasions in the whole history of the world. 此时此刻,通过现代通信手段的奇迹,看到和听到我们讲话的人比整个世界历史上任何其他这样的场合都要多。(部分倒置) (2)I believe strongly that it is in the interest of my countrymen that Britain should remain an active and energetic member of the European Community. 我坚信,英国依然应该是欧共体中的一个积极的和充满活力的成员,这是符合我国人民利益的。(部分倒置) (3)改革开放以来,中国发生了巨大的变化。 Great changes have taken place in China since the introduction of the reform and opening policy.(全部倒置) 7.倒置法: 在汉语中,定语修饰语和状语修饰语往往位于被修饰语之前;在英语中,许多修饰语常常位于被修饰语之后,因此翻译时往往要把原文的语序颠倒过来。倒置法通常用于英译汉, 即对英语长句按照汉语的习惯表达法进行前后调换,按意群或进行全部倒置,原则是使汉语译句安排符合现代汉语论理叙事的一般逻辑顺序。有时倒置法也用于汉译英。如: (1)At this moment, through the wonder of telecommunications, more people are seeing and hearing what we say than on any other occasions in the whole history of the world.
十四种雅思阅读题型做题技巧 一、Matching(从属关系搭配题) 1.题型要求 Matching(搭配题)是IELTS最常考的题型之一,每次考试至少有一组,很多时候达到两组甚至更多,应该引起同学们的重视。搭配题通常有三部分组成:题目要求、选相的集合、题目的集合。要求你根据某种关系将题目与选项配对。这种关系在题目要求中说明。搭配题通常不具有顺序性,也就是说,题目的顺序和原文的顺序是不一致的。所以做搭配题,通读一遍原文一般是不可避免的。大多数同学会感觉这种题型不太难,但比较烦。如果有足够的时间,肯定都能做出来。这种题型就是考大家的快速阅读能力,即很快从文章中找到所需信息的能力。大家在做搭配题的练习时,不仅要保证准确率,还要注意时间。一般每个题目1-2分钟。例如一组6个题目的搭配题,应在8-10分钟做完。搭配题本身有分为三种类型:从属关系搭配题、因果关系搭配题、作者及其观点搭配题。 不同类型的搭配题有不同的解题方法,所以我分为三种题型分别介绍,希望这样会更清楚。本节主要介绍从属关系搭配题。从属关系搭配题是搭配题中最常靠的类型。选项中的元素和题目中的元素是从属的关系,要求根据原文,将每个题目与相应的选项搭配。 请看下面中文阅读例子: 原文:介绍中国四个直辖市的情况。(略) 题目要求:将直辖市的特征与相应的城市搭配。 选项:A 北京市B 上海市 C 天津市D 重庆市 题目:1 狗不里包子2 黄浦大桥3 天安门4 十八街麻花 答案:1C 2 B 3A 4C 考试中,A类和G类一般都是每次必考,考两组,共十题左右。有时也考一或三组。 2.解题步骤 (1)仔细阅读题目要求,搞清选项和题目之间的关系。 虽然都是从属关系,但也有很大的不同。有的是汽车制造公司和它们的设计特点,有的是俱乐部和它们举办的活动等等。所以在做题前一定要仔细阅读题目要求,搞清选项和题目之间的关系。 (2)先把题目从头到尾看一遍,尽可能多记些关键词。做这种题,通读一遍原文一般是不可避免的,但最好只读一遍原文。能做到这点的前提是:在读原文之前,先把题目从头到尾看一遍,记住尽可能多的题目中关键词。这样,在读文章时,就知道要找什么东东。例如,前面介绍的中文阅读文章,在做题前应看以下1-4题,知道要找:狗不里包子、黄浦大桥、天安门、十八街麻花。在读文章是,就特别注意这些词。这么做的主要原因是因为这种题型没有顺序性,如果只看第1题:狗不理包子,就阅读原文。狗不理包子的描述在原文任何位置都有可能,很有可能就在文章的结尾处。这样,你读完一遍文章,只做了一个第1题,做第2题时,你还需要从头再阅读原文,这样很浪费时间。这一步是做这种题型的关键,否则,就会造成反复地读原文,浪费时间。 (3)从头到尾快速阅读原文,遇到所记住的关键词或其对应词,当即解答该题。从头到尾依顺序快速阅读原文,在阅读原文时,注意寻找所记住的题目中的关键词,如果关键词是专用名词或很生僻的词,一般在原文中出现的就是该词本身,否则会有同义词或同义表述的对应。选项常常是一些专用名词,包含大写字母。这时,在阅读原文时,应特别注意包含大写字母的地方,注意其前后的词是否与所记住的关键词相同或相对应。在阅读原文是,要特别注意原文中一些有特别标记的词,如反复出现的词、括好里的词、引号里的词、黑体字、斜体字,这些词常常是题目中的关键词或其改写。如果关键词比较抽象,比如是专有名词或者很生僻的词,不好记忆,大家也不要害怕。这可能是件好事,在原文中出现的很可能就是该词本身。所以即使记不住,在阅读原文时,可以采用边读文章边看选项的方法。因为在读原文之前,已把题目从头到尾看了一遍,所以最好只读一遍文章就能做出绝大多数的题目。比如一组6个题目,能找到4-5个。 (4)解答没有匹配上的题目。由于有的关键词没有记住,或者有的与原文没有对应上。读完一遍文章后,有的题目没有找出来。比如一组6个题目,1-2个没能找到。这已是很不错的表现了。对于这1-2个题目,可以有如下的解决办法:
表面等离子体激元简介一.表面等离子体激元表面等离子体(Surface Plasmons)的出现提供了一种在纳米尺度下处理光的方式。表面等离子体通常可以分成两大类——局域表面等离子体共振(Localized Surface Plasmon Resonance)和表面等离子体激元(Surface Plasmon Polaritons)。局域表面等离子体共振专指电磁波与尺寸远小于波长的金属纳米粒子中的自由电子的相互耦合,这种等离子体只有集体共振行为,不能传播,但可以向四周环境辐射电磁波。局域表面等离子体共振可以通过光直接照射产生。表面等离子体激元指的是在金属和电介质分界面上传播的一种元激发Excitations),这种元激发源自电磁波和金属表面自由电子集体共振的相互耦合。表面等离子体激元以指数衰减的形式束缚在垂直于传播的方向,由于它的传播波矢要大于光在自由空间中的波矢,电磁波被束缚在金属和电介质的分界面而不会向外辐射,也正是因为这种独特的波矢特性,表面等离子体激元的激发需要满足一定的波矢匹配条件。二.SPPs的激发和仿真方法由于SPSs的波矢量大于光波的波矢量,或者说SPPs的动量与入射光子的动量不匹配,所以不可能直接用光波激发出表面等离子体波。为了激励表面等离子体波,需要引入一些特殊的结构达到波矢匹配,常用的结构有以下几
种:(1)棱镜耦合:棱镜耦合的方式包括两种,一种是Kretschmannt方式;另一种是Otto方式。(2)采用波导结构(3)采用衍射光栅耦合(4)采用强聚焦光束(5)采用近场激发。目前主要的仿真方法有以下三种(1)时域有限差分法(finite difference time domain,FDTD):FDTD方法是把Maxwell方程式在时间和空间领域上进行差分模拟,利用蛙跳式(leaf flog algorithm)空间领域内的电场和磁场进行交替计算,电磁场的变化通过时间领域上更新来模仿。优点是能够直接模拟场的分布,精度比较高,是目前使用较多的数值模拟方法之一。(2)严格耦合波法(rigorous coupled—wave analysis,RCWA):该方法是分析光栅的有利工具,它是基于严格的矢量maxwell 方程来分析。由于在很多的表面等离子的结构中都会引入衍射光栅结构,所以RCWA方法也被越来越多的学者用来分析相关的问题,并且取得了不错的效果。(3)限元法(finite element method,FEM):该方法是从变分原理出发,将定义域进行有限分割,离散成有限个单元集合。通过区域剖分和分偏差值,把二次泛函的极值问题化为普通多元二次函数的极值问题,后者等价于一组多元线性代数方程的求解。该方法分析的是一种近似结果,不过很多的问题能近似模拟,目前应用也比较广泛。三.SPPs的若干应