
外文文献资料
收集:苏州大学应用技术学院11电子班(学号1116405026)马玲丽
Image Information Hiding: An Survey
I. INTRODUCTION
Nowadays many problems arise during the image transformation from the sender to the receiver. Strangers can easily snoop into others account and get many secret information even it was hided by some mechanism, without their permission. To avoid this we propose a secure scheme by using steganography concept. Steganography means hiding information in a particular way that prevents the detection of hidden information. In this concept no one can find that there is a hidden message present in the image, Because of information is hidden behind an image in a matrix form, which is created by bit matrix of the object. By using the LSB we can store the characteristics of particular pixels of an image are modified to store a message. Finally we send the final picture and cover image used for hidden the image to the receiver [Johnson & Jajodia, 1998].
At first we calculate the height and width of the image, which hide the information then multiply it with 8 and store it in any value. Then we calculate the height and width of the image which is used to hide the object and multiply with each other. Then we compare that answers with both the image which is used to hide the information and which is used to hide the object. The image which is used to hide the object must have greater value than the other image; we choose the object must satisfy the above condition. Then the encoded matrix is mapped with the image by using least significant bit mechanism.
Least significant bit only stores the information instead of replacing the pixel of image. So scattering of information takes place while transferring the image so according to human eye there is no difference between the original and stego image. Finally sender sends the both original and stego image to the receiver. In the receiver side to get the information the receiver must do XOR operation
between bytes present in both the image. Compare the result with 0*00000000 If the output will be yes then store 0 else 1 in a matrix and this matrix will be equal to the width and height of the pixel matrix of the image. Convert the bits into bytes until all bits got utilized. Finally receiver gets the information.
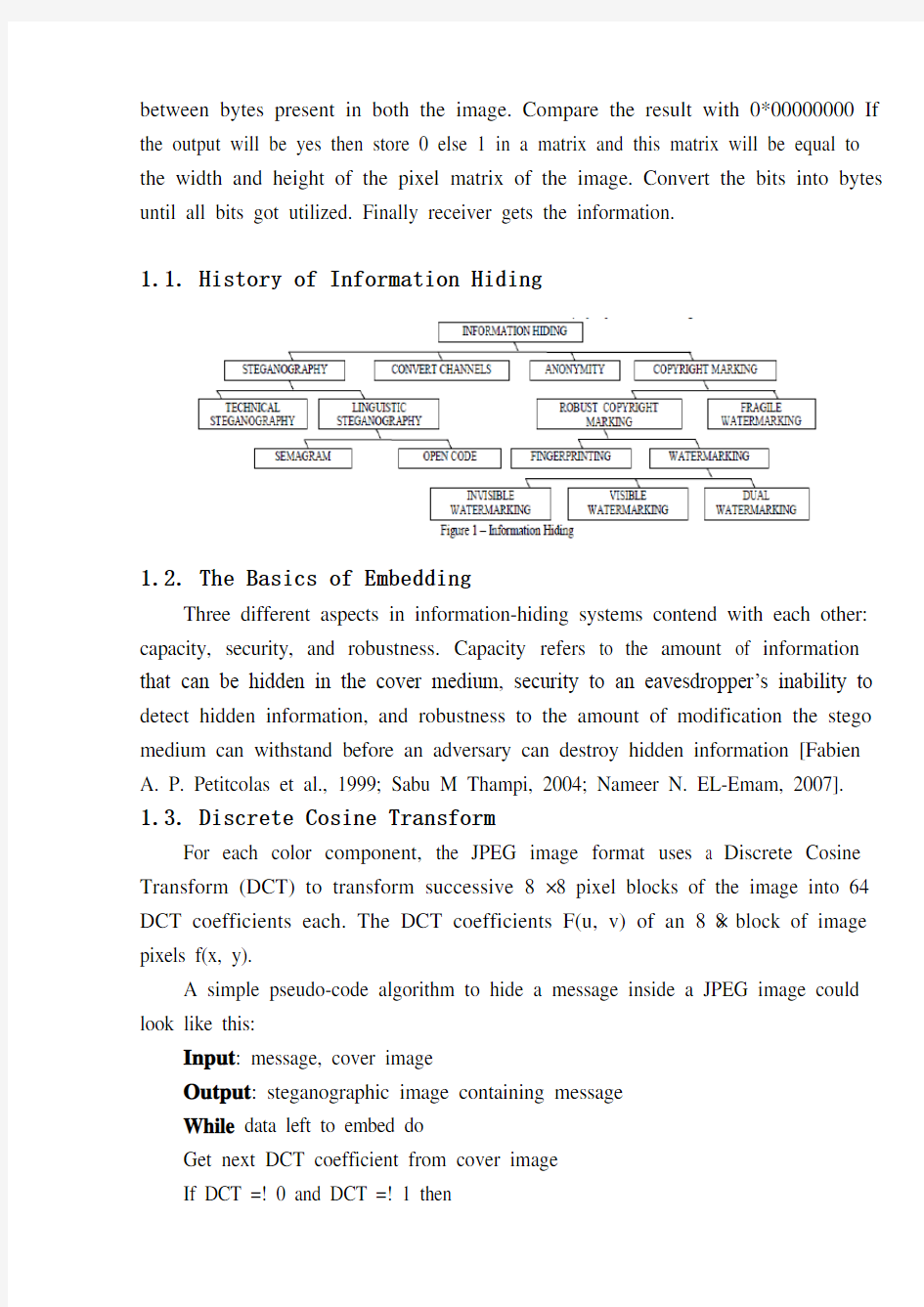
1.1. History of Information Hiding
1.2. The Basics of Embedding
Three different aspects in information-hiding systems contend with each other: capacity, security, and robustness. Capacity refers to the amount of information that can be hidden in the cover medium, security to an eavesdropper’s inability to detect hidden information, and robustness to the amount of modification the stego medium can withstand before an adversary can destroy hidden information [Fabien
A. P. Petitcolas et al., 1999; Sabu M Thampi, 2004; Nameer N. EL-Emam, 2007].
1.3. Discrete Cosine Transform
For each color component, the JPEG image format uses a Discrete Cosine Transform (DCT) to transform successive 8 × 8 pixel blocks of the image into 64 DCT coefficients each. The DCT coefficients F(u, v) of an 8 × 8 block of image pixels f(x, y).
A simple pseudo-code algorithm to hide a message inside a JPEG image could look like this:
Input: message, cover image
Output: steganographic image containing message
While data left to embed do
Get next DCT coefficient from cover image
If DCT =! 0 and DCT =! 1 then
Get next LSB from message
Replace DCT LSB with message bit
End if
Insert DCT into steganographic image
End while
1.4. Detection Techniques
Many algorithms were proposed for estimating the length of the secret message in the cover image. Westfeld (2001) proposed the blind steganalysis based on statistical analysis of PoVs (pairs of values). This method, so-called statistical test, gives a successful result to a sequential LSB steganography only. Fridrich et al. proposed the RS steganalysis. This method makes small alternations to the least significance bit plane in an image the by using the following method our process [Kekre et al., 2008; Bin Li et al., 2011].
1.5. Security the Packet Decoder
The decode engine is organized around the layers of the protocol stack present in the supported data-link and TCP/IP protocol definitions. Each subroutine in the decoder imposes order on the packet data by overlaying data structures on the raw network traffic. These decoding routines are called in order through the protocol stack, from the data link layer up through the transport layer, finally ending at the application layer. Speed is highlight in this section, and the majority of the functionality of the decoder consists of setting pointers into the packet data for later analysis by the detection engine [Richard Popa, 1998].
1.6. Internet Protocol Version
Internet Protocol version 6 (IPv6) is a network layer IP standard used by electronic devices to exchange data across a packet-switched internetwork. It follows IPv4 as the second version of the Internet Protocol to be formally adopted for general use. Among the improvements brought by IPv6 is the increase of
addresses for networked devices, allowing, for example, each cell phone and mobile electronic device to have its own address. IPv4 supports 4.3×109 (4.3 billion) addresses, which is inadequate for giving even one address to every living person, much less support the burgeoning market for connective devices. IPv6 supports 3.4×1038 addresses, or 5×1028(50 octillion) for each of the roughly 6.5 billion people alive today.
Normally the packets are transferred from one system to another in packets. The packets are transferred through the tcp connection in a more secure way.
II. HIDE AND SEEK: AN INTRODUCTION TO STEGANOGRAPHY
2.1. Problem Formulation
In the past, for the security purpose people used hidden tattoos or invisible ink to convey steganographic content. Today for hiding purpose computer and network technologies provide easy-to-use communication channels for steganography [Saraju P. Mohant, 2003; Muhalim Mohamed Amin et al., 2003].
Steganographic system because of their invasive nature, leave the detectable traces in the cover medium. The secret content is not revealed, but its statistical properties changed so the third party can detect the distortions in the resulting image [Morkel et al., 2005]. The process of finding the distortions is called statistical steganalysis.
2.2. Research Design
This paper explains the steganagraphic systems and presents the recent research in detecting them through statistical steganalysis.
Steganographic systems for the JPEG format seem more interesting, because the systems operate in a transform space and are not affected my visual attacks.
Visual attacks mean that we can see steganographic images on the low bit planes of an image because they overwrite the visual structures.
2.3. Finding
The JPEG image format uses a discrete cosine transform to transform successive 8*8 pixel blocks of the image into 64 DCT coefficients each. The SIJ Transactions on Computer Science Engineering & its Applications (CSEA), V ol. 1,
No. 1, March-April 2013 ISSN: 2321 – 2381 ? 2013 | Published by The Standard International Journals (The SIJ) 3
The embedding algorithm sequentially replaces the least significant bit of DCT coefficients with the message data. The same process is also done in the JPEG format.
The author and his colleague used a support vector machine to create a nonlinear discrimination function. Then they present a less sophisticated but easier to understand method for determining a linear discrimination function.
2.4. Conclusion and Limitations
We offer four details for our inability to find steganographic content on the internet. They are,
·All steganographic system users carefully choose passwords that are not susceptible to dictionary attacks.
·May be images from sources we did not analyze carry steganographic content.
·Nobody uses steganographic systems that we could find.
·All messages are too small for our analysis to detect.
Although steganography is applicable to all data objects that contain redundancy, we consider JPEG images only for steganography.
2.5. Implications
We insert the tracer images into every stegbreak job. The dictionary attack follows the correct passwords for these images.
III. STEGANOGRAPHY AND STEGANALYSIS
3.1. Problem Formulation
The growth of computer networks and internet has explored means of business, scientific, entertainment, and social opportunities.
The digital information can be easily duplicated and distributed has led to the need for effective copyright protection tools such as steganography and cryptography [Stefano Cacciaguerra & Stefano Ferretti, 2003; Robert Krenn,
2004].
3.2. Research Design
Secrets can be hidden inside all sorts of cover information: text, images, audio, video and more. Most steganographic utilities nowadays, hide information inside images, as this is relatively easy to implement [Christian Cachin, 1998].
Hiding information inside images is a popular technique nowadays [Shashikala Channalli, 2009]. An image with a secret message inside can easily be spread over the World Wide Web or in newsgroups.
The most common methods to make alterations in the image present in noisy area involve the usage of the least-significant bit or LSB, masking, filtering and transformations on the cover image. These techniques can be used with varying degrees of success on different types of image files.
3.3. Finding
More techniques are developed for hiding the information to detect the use of steganography. While the information can be hidden inside texts in a way that the message can only be detected with the knowledge of the secret key.
A widely used technique for image scanning involves statistical analysis, with the statistical analysis on the lsb, the difference between random values real image value can easily be detected.
The statistical analysis method can be used against the audio files too, since the lsb modification technique can be used on sounds too, including that several other things also detected.
While steganograms may not be successfully detected instead of that we use the statistical analysis from possible cover sources.
3.4. Conclusions and Limitations
Steganography combined with cryptography is a powerful tool which enables people to communicate without possible eavesdroppers even knows that there is a communication in the first place.
Steganography might also become limited laws, since government already claimed that criminals use these techniques to communicate. More restrictions are
provided in the time of terrorist attacks.
3.5. Implications
In the future the most important use of steganographic techniques will lie in the field of digital watermarking. Content providers are eager to protect their copyrighted works against illegal distribution and digital watermarks provide a way of tracking the owners of these materials.
Although it will not prevent the distribution itself, it will enable the content provider to start legal actions against the violators of the copyrights, as they can now be tracked down.
IV. HIDING ENCRYPTED MESSAGE IN THE FEATURES OF IMAGES
4.1. Problem Formulation
Steganography is the art and science of writing hidden messages in such a way that no one can’t know about the intended recipient knows the existence of the message. It simply takes one piece of information and hides it with another [Kh. Manglem Singh et al., 2007].
4.2. Research Design
This process explains the least significant bit embedding algorithm for hiding encrypted messages in nonadjacent and random pixel locations in edges of images. It first encrypts the secret message and detects image in the cover image.
The simplest way to hide data on an image is to replace the least significant bits of each pixel sequentially in the scan lines across the image in raw image format with the binary data.
An attacker can easily see the message by repeating the process. To avoid this to add better security, the message to be hidden is first encrypted using the simplified data encryption standard and then it is distributed randomly by a pseudo random number generator across the image.
4.3. Finding
Many algorithms are used to estimate the length of the secret message in the cover image. Here they propose the blind steganalysis based on statistical analysis of pairs of values. This method is called statistical test.
They propose the detection algorithm based on higher order statistics for separating original images from stego images.
Blind detection algorithm that estimates the accuracy of embedded message through the analysis of the variation of the energy resultant from the lsb embedding.
4.4. Conclusions and Limitations
The paper described a novel method for embedding secret message bit in least significant bit of nonadjacent and random pixel locations in edges of images. No original cover image is required for the extraction of the secret message. It has been shown experimentally that the blind LSB detection technique like the gradient energy method could not estimate the length of the secret message bits accurately for the proposed algorithm.
4.5. Implications
The message to be hidden in the image was first encrypted using the S-DES algorithm. Then estimate the length of the secret message bits by the gradient energy technique. Gradient energy technique could not estimate the length of the secret message bit accurately.
4.6. Advantages
A message in cipher text, for instance, might arouse suspicion on the part of the recipient while an “invisible” message created with steganographic met hods will not.
Watermarking is either “visible” or “invisible”. Although visible and invisible are visual terms watermarking is not limited to images, it can also be used to protect other types of multimedia object.
In steganographic communication senders and receivers agree on a steganographic system and a shared secret key that determines how a message is encoded in the cover medium. Without the key they can’t identify the secret
message.
In steganographic systems the images we used for hiding may be JPEG format seem more interesting because the systems operate in a transform space and are not affected by visual attacks.
4.7. Disadvantages
Encryption protects contents during the transmission of the data from the sender to receiver. However, after receipt and subsequent decryption, the data is no longer protected.
By using the secret key we are deliver the secret message safer at the same time if any hacker finds the key then they can easily get the secret message.
Visual attacks mean that you can see steganographic messages on the low bit planes of an image because they overwrite visual structures; this usually happens in BMP images.
V. PROPOSED SYSTEM
Steganography is used to hide the information in the form of multimedia objects considering two things that is size and degree of security.
This concept assists the scattering of information at the time of hiding and implements the non traceable randomization to differentiate from the existing work.
Double embedding is done for more security.
5.1. Advantages
Steganography is the concept of hidden messages in such a way that no one apart from the intended recipient knows of the existence of the message. Here double embedding takes place. So it is safer.
It doesn’t have any key to decrypt the ima ge. So the hacker has no chance to get the message in this way.
This concept deals that the eavesdroppers will not have any suspicion that message bits are hidden in the image and standard steganography detection methods can not estimate the length of the secret message correctly.
With steganography we can send messages without anyone having knowledge of the existence of the communication.
There are many countries where it is not possible to speak as freely as it is in some more democratic countries. Then it is the easy method to send news and information without being censored and without the fear of the messages being interrupted.
5.2. Disadvantages
This concept is applied only for images not for audio and video files.
The receiver must know about the least significant bit technique.
VI. CONCLUSION
Here we conclude that we prevent the detection of hidden information by using steganography concept and propose a The SIJ Transactions on Computer Science Engineering & its Applications (CSEA), V ol. 1, No. 1, March-April 2013 ISSN: 2321 –2381 ? 2013 | Published by The Standard International Journals (The SIJ) 5 secure scheme for image transformation. Here we use least significant Bit modification technique to insert the image into another image for hidden purpose. Image is hidden into another image is the technique we introduced in our paper. In other security mechanisms the strangers can easily stole the message from the image by repeating the process. But in our technique without the stego key we can’t extract the message from the image. This technique facilitates the scattering of information at the time of hiding; this is new method we proposed in our paper.
VII. FUTURE ENHANCEMENT
Apart from this, any kind of future endeavor in this field will definitely route it a path to design a secure system using the proposed algorithm for both Internet and Mobile Communication Technology. The scattering of information technique is used at the time of hiding is useful for many news papers based on steganography. Development in covert communications and steganography will research in building more robust digital watermarks that can survive image manipulation and attacks. We hope some commercial and effective schemes will be
available in future. In the near future, the most important use of steganographic techniques will probably lie in the field of digital watermarking. Content providers are eager to protect their copyrighted works against illegal distribution and digital watermarks provide a way of tracking the owners of these materials. In future we can use this paper in the Government, Software Company, Detective agencies etc. The same step is involved to embed the information and send to particular user.
REFERENCES
[1] N.F. Johnson & S. Jajodia (1998), “Exploring Steganography: Seeing the Unseen Computer”, Vol. 31, No. 2, Pp. 26–34. [2] Richard Popa (1998), “An Analysis of Steganographic Techniques”, Pp. 1–17. [3] Christian Cachin (1998), “An Information-Theoretic Model for Steganography”, Information Hiding, Lecture Notes in Computer Science, V ol. 1525, Pp 306-318. [4] Fabien A. P. Petitcolas, Ross J. Anderson & Markus G. Kuhn (1999), “Information Hiding –A Survey”, Proceedings of the IEEE, Special Issue on Protection of Multimedia Content, V ol. 87, No. 7, Pp. 1062–1078. [5] A. Westfeld (2001), “F5-A Steganographic Algorithm: High Capacity Despite Better Steganalysis”, Proceedings of 4th International Workshop Information Hiding, Pp. 289–302. [6] Saraju P. Mohant (2003), “Digital Watermarking: A Tutorial Rev iew Niels Provos, Peter Honeyman, Hide and Seek: Introduction to Steganography”. [7] Muhalim Mohamed Amin, Subariah Ibrahim, Mazleena Salleh & Mohd Rozi Katmin (2003), “Information Hiding using Steganography”, Information Hiding using Steganography Approach , V ol. 71847, Pp. 1–34. [8] Stefano Cacciaguerra & Stefano Ferretti (2003), “Data Hiding: Stegnography and Copyright Marking”, Department of Computer Science, University of Bologna, Italy, Pp. 1–30. [9] Robert Krenn (2004), “Steganography and Steganalysis”. [10] Sabu M Thampi (2004), “Information Hiding Techniques: A Tutorial Review”, ISTE-STTP on Network Security & Cryptography, LBSCE 2004. [11] T. Morkel, JHP Eloff & MS Olivier (2005), “An Overview of Image Steganography”, Proceedings of the Fifth Annual Information Security South Africa Conference(ISSA2005), Sandton, South Africa. [12] Nameer N. EL-Emam (2007), “Hiding a Large Amount of Data with High Security using Steganography”, Algorithm Journal of Computer Science, Vol. 3, No. 4, Pp. 223–232. [13] Kh. Manglem Singh, S. Birendra Singh & L. Shyam Sundar Singh (2007), “Hiding Encrypted Message in the Features of Images”, International Journal of Computer Science and Network Security (IJCSNS), V ol. 7, No.
4. [14] H.B. Kekre, Archana Athawale & Pallavi N. Halarnkar (2008), “Increased Capacity of Information Hiding in LSB’s Method for Text and Image”, World Academy of Science, Engineering and Technology, Pp. 910–913. [15] Shashikala Channalli (2009), “Steganography: An Art of Hiding Data”, International Journal on Computer Science and Engineering, V ol. 1, No. 3, Pp 137–141. [16] Bin Li, Junhui He, Jiwu Huang, Yun Qing Shi (2011), “A Survey on Image Steganography and Steganalysis”, Journal of Information Hiding and Multimedia Signal Processing, V ol. 2, No. 2, Pp. 142–171. D. Saravanan c urrently working as an Assistant Professor in the department of computer applications in Sathaybama University, Chennai. His areas of interest are image processing, data mining, DBMS. He has published paper in five national conferences & two international journals in the field of data mining. A. Ronold Doni working as an Assistant Professor in the department of computer applications in Sathaybama University, Chennai. His areas of interest are image processing, data mining, DBMS. He has published paper in three national conferences & one international journal in the field of data mining. A. Abisha Ajith studying First Year MCA in Sathyabama University, Chennai. Her areas of interest are image processing, data mining, DBMS. She has published paper in one national conference & one international journal in the field of data mining.
中文翻译稿
翻译:苏州大学应用技术学院11电子班(学号1116405026)马玲丽
图像信息隐藏:调查
1.介绍
现如今从发送端到接收端的图像变换过程中出现了许多问题。陌生人未经其许可,可以很容易地探听他人帐户并获得许多的秘密信息,甚至是一些被隐藏的机制。为了避免这种情况,我们利用隐写术的概念提出了一个安全的方案。隐写术意味着隐藏的信息在一个特定的方式,为防止其检测隐藏的信息。在这个概念中,没有人可以发现图像中有一个隐藏的信息存在,因为信息隐藏在一个由对象位矩阵组成的矩阵形式中。通过使用LSB,我们可以存储被修改的特定的图像像素的特征来存储信息。最终,我们发送最后一张图片并且覆盖它以用于接收器隐藏图像[约翰逊&雅茱蒂,1998 ]。
首先计算隐藏信息的图像的高度和宽度,再乘以8,并将其存储在任何价值中。然后我们计算用于隐藏对象,并与之互乘的图像的高度和宽度。然后比较图像用于信息隐藏与用于隐藏对象的图案之间的答案。用来隐藏对象的图像必须比其他图像具有更高的价值;我们所选择的对象必须满足上述条件。然后编码矩阵通过使用最低有效位机制映射图像。
最低有效位只存储信息,而不是取代图像的像素。因此信息的散射发生在传输图像的时候,根据人眼无法区别原始和隐秘图像之间的差别。最后,发送端发送原始和隐秘图像给接收端。在接收端一方,为了获取信息,接收端必须在图像的当前字节之间做异或运算。结果与0 * 00000000比较,如果输出将是是的话,那么在矩阵中存储为0否则为1,该矩阵将等于图像像素矩阵的宽度和高度。将位转换为字节,直到所有位得到利用。最后接收端获取信息。
1.1信息隐藏的历史
1.2嵌入基础
在信息隐藏系统三个不同方面相互抗衡:能力,安全性,和鲁棒性。能力指的是能够隐藏在覆盖的媒介中的信息量,安全性对窃听者来说是无法察觉到隐藏的信息,而鲁棒性的修正,使隐藏介质可以在敌人摧毁隐藏的信息之前承受这种摧毁。[法比安. 普提特克拉斯等人, 1999; 萨布玛琪, 2004; 南耶. 埃尔-埃南, 2007].
1.3离散余弦变换
每个颜色分量,JPEG图像格式采用离散余弦变换(DCT)将连续8×8像素的图像块的DCT系数都为64。DCT系数F(u,v)8×8块的图像像素F(x,y)。
一个简单的伪代码算法隐藏在JPEG图像的消息可能看起来像这样:
输入:信息,覆盖图像
输出: 包含信息的隐写图像
当数据向左嵌入
从覆盖图像中得到下一个DCT系数
如果DCT = !0和DCT = !1那么
得到下一个LSB信息
从信息获取下一个LSB
在消息位取代DCT LSB
如果结束
把DCT插入到隐写图像
最后结束
1.4检测技术
提出了许多在覆盖图像中估算秘密信息的长度的算法。韦斯特菲尔德(2001)提出了基于统计分析的盲隐写式密码解密的观点(双值)。这种所谓的统计测试的方法, ,给出了一个顺序LSB隐写术成功的结果。弗雷德里奇等人提出了RS隐写分析。这种方法产生了小的改变,使最不重要位平面的图像通过我们的过程使用以下方法 [科克鲁等人,2008;本李等人,2011)。
1.5安全包解码器
解码引擎是围绕支持数据链和TCP / IP协议定义的协议栈的层次被组织的。译码器中的每个子程序的分组数据通过在原始网络流量叠加数据结构。这些解码程序被称为通过协议栈,从数据链路层到传输层,最后结束在应用程序层。速度是本节中的亮点,大多数解码器的功能包括在数据包中设置指针,通过检测引擎供以后分析[理查德波帕, 1998]。
1.6互联网协议版本
互联网协议版本6(IPv6)是一个网络层IP标准通过使用电子设备在分组交换的互联网络交换数据。它遵循IPv4作为互联网协议的第二个版本,被正式通过普遍使用。IPv6带来的改进之一是网络设备地址的增加,允许,例如,每个手机和移动电子设备有它自己的地址。IPv4的支持4.3×109(4300000000)的地址,这甚至连每一个活着的人一个地址都不够给的,更不用说来支持新兴市场连接设备。IPv6为了每一个活着的约65亿人支持3.4×1038个地址,或5×1028(50千的九次方)。
通常情况下,数据包在数据包中从一个系统转移到另一个系统。通过tcp连接的数据包传输方式更安全。
2.捉迷藏:隐写术简介
2.1问题描述
在过去,为安全目的的人使用隐藏的纹身或隐形墨水传递隐藏信息。今天的隐藏目的计算机和网络技术为隐写术易于使用的沟通渠道;[Saraju P. Mohant, 2003; 穆哈林穆罕默德阿明等人,2003 ]。
隐写系统由于其侵袭性,把检测的痕迹在覆盖介质。秘密内容没有透露,但其统计特性改变扭曲的第三方可以检测结果图像(默克尔等人,2005)。发现变形的过程称为统计分析。
2.2研究设计
本文阐述了隐写术系统,提出了最近通过统计隐写式密码解密检测的研究。
为JPEG格式的隐写系统显得更有趣,因为系统在变换空间,不影响我的视觉攻击。
视觉的攻击意味着我们可以看到隐写图像,在图像低比特平面因为他们覆盖的视觉结构。
2.3发现
JPEG图像格式使用离散余弦变换变换连续8×8像素的图像块的DCT系数都为64。计算机工程与应用SIJ交易(CSEA),卷1,1号,2013月四月刊号:2321–2381?2013 |由国际标准期刊(SIJ)3
嵌入算法依次替换的DCT系数的消息数据的最低有效位。同样的过程也在JPEG格式做了。
作者和他的同事用支持向量机建立一个非线性判别函数。然后,他们提出了一个不太复杂的但更容易理解,确定一个线性判别函数法。
2.4结论和局限性
我们提供四的细节,我们不能在互联网上找到隐藏的内容。他们是,
?所有的隐写系统用户精心选择的密码,不容易受到字典攻击。
?可能来源于我们没有携带隐藏信息的图像分析。
?无人使用的隐写系统,我们可以找到。
?所有信息为我们的分析检测太小。
虽然隐写术适用于所有数据对象包含冗余的,我们考虑的JPEG图像隐写术仅为。
2.5影响
我们插入示踪图像到每一个隐藏信息系统工作。字典攻击之前,这些图像正确的密码。
3.信息隐藏和隐写分析
3.1问题描述
计算机网络和互联网的发展探索了意味着商业,科学,娱乐,和社会的机会。
数字信息可以很容易地复制和分布有LED为有效的版权保护工具,如信息隐藏和加密[斯蒂法诺卡西格拉 &斯蒂法诺弗瑞提,2003;罗伯特,克伦,2004 ]。
3.2研究设计
秘密被隐藏在各种覆盖信息:文本,图像,音频,视频和更多。大多数隐写工具目前,在图像信息隐藏,这是比较容易实现的[基督教加香,1998 ]。
现在隐藏信息在图像中是一种流行的技术[萨斯卡拉陈娜莉,2009]。图片里面有秘密信息可以很容易地分布在万维网或新闻组。
最常见的方法,在嘈杂的区域的图像现在做出改变涉及的最不重要位或LSB,使用屏蔽,滤波和变换的封面图像。这些技术可用于不同程度的成功,在不同类型的图像文件。
3.3发现
更多的技术开发的隐藏信息检测的隐写术。虽然信息可以隐藏在文本中的一种方式,消息只能用的秘密密钥的知识发现。
一种广泛使用的图像扫描技术涉及的统计分析,以统计分析的LSB,随机值的实时图像值之间的差异可以很容易地被检测到。
统计分析方法可用于对音频文件,从LSB的改性技术可用于听起来太,包括一些其他的事情也发现。
而隐藏信息系统可能无法成功检测到的而不是我们使用可能覆盖源的统计分析。
3.4结论和局限性
信息隐藏与加密技术相结合,是一个功能强大的工具,它使人们的沟通不可能窃听者都知道,这是摆在首位的通信。
隐写术也可能成为公司的法律,因为政府已经声称,犯罪分子利用这些技术交流。更多的限制是恐怖袭击的时间设置。
3.5影响
在未来最重要的使用隐写术将数字水印领域的撒谎。内容提供商急于保护自己的版权作品反对非法分布和数字水印提供跟踪这些材料的主人的一种方式。
虽然它不会阻止分布本身,它将使内容提供商开始对侵犯版权的法律行动,因为他们现在可以跟踪。
4.隐藏图像的加密信息的特征
4.1问题公式化
隐写术是在这样一种方式,没有人不知道收件人知道消息的存在隐藏消息写作的艺术和科学。它只需要一条信息隐藏与另一个[客汗
王格棱兴等人,2007 ]。
4.2研究设计
这个过程解释了最低有效位嵌入算法隐藏加密信息在不相邻和随机像素位置的边缘图像。它首先加密机密信息和检测图像的封面图片。
隐藏一个图像数据的最简单方法是将每个像素的最低有效位顺序在对面的扫描线图像原始图像格式的二进制数据。
攻击者可以很容易地看到消息通过重复这个过程。为了避免这种添加更好的安全性,要隐藏的消息首先是使用简化的数据加密标准加密,然后随机分布的伪随机数发生器的形象。
4.3发现
许多算法用于估计秘密信息的长度在封面图片。在这里他们提出基于统计分析的盲隐写式密码解密的双值。这种方法叫做统计检验。
他们提出的基于高阶统计量检测算法将原始图像从隐藏图像。
盲检测算法估计嵌入信息的准确性的分析变异的能量合成lsb嵌入。
4.4结论和局限性
本文描述了一种新颖的方法,将秘密信息嵌入不相邻的最低有效位和随机像素位置的边缘图像。不需要原始封面图片的提取秘密信息。有实验表明,盲人LSB检测技术如梯度能量法无法估计秘密信息的长度对提出的算法准确。
4.5影响
要隐藏在图像的消息首次使用源加密算法。然后估计秘密信息的长度位梯度能源技术。梯度能量技术不能准确估计秘密信息的长度。
4.6优势
在密文信息,例如,可能会引起怀疑的接受者而创建了一个“看不见”的信息隐写方法将不是。
水印是“可见”或“隐形”。虽然各种有形和无形的视觉条件水印并不局限于图片,它还可以用来保护其他类型的多媒体对象。
在隐通信发送方和接收方的同意隐写术系统和一个共享密钥,用来决定盖中是如何编码的消息。没有他们不能确定秘密信息的关键。
在隐写系统用于隐藏的图片我们可以JPEG格式看起来更有趣,因为系统在转换经营空间和不受视觉攻击。
4.7缺点
在传输数据的加密保护内容从发送方到接收方。然而,在收到和随后的解密,数据不再是受保护的。
通过使用我们提供的密钥的秘密信息安全的同时如果任何黑客发现的关键然后他们可以很容易地获得秘密信息。
视觉攻击意味着你可以看到图像的隐写低一点的飞机上的消息,因为它们覆盖视觉结构,这通常发生在BMP图像。
5.提出系统
隐写术是用来隐藏信息的多媒体对象的形式考虑两件事,是大小和程度的安全。
这个概念助攻时的散射信息隐藏和实现了非可追踪的随机化区分从现有工作。
双重嵌入更多安全完成。
5.1优势
隐写术是信息隐藏在这样的概念没有人除了收件人知道存在的消息。这里双重嵌入。所以它是安全的。
它没有任何解密图像的关键。因此,黑客没有机会得到这样的消息。
这一概念上,窃听者不会有任何怀疑消息位隐藏在图像隐写术和标准检测方法不能正确估计秘密信息的长度。
隐写术我们可以发送消息,没有人有知识存在的沟通。
有很多国家是不可能说话一样自由地在一些民主国家。那么简单的方法发送新闻和信息没有被审查和没有恐惧的消息被打断。
5.2缺点
这个概念仅适用于图像没有音频和视频文件。
接收方必须知道最低有效位的技术。
6.结论
在这里,我们得出结论,我们防止隐藏信息的检测通过使用隐写术的概念和计算机工程与应用提出了一个SIJ交易(CSEA),卷1,1号,2013月四月刊号:2321–2381?2013 |由国际标准期刊(SIJ)5安全的图像变换方案。在这里,我们使用最低有效位的改性技
术将图像插入到另一个图像隐藏的目的。图像隐藏到另一个图像技术引入我们的论文。在其他安全机制的陌生人可以很容易地偷走了信息从图像重复的过程。但在我们的技术不隐写密钥不能从图像中提取的信息。这种技术有利于散射信息隐藏的时代;这是我们在我们的论文中提出的新方法。
7.未来的增强
除此之外,在这一领域的任何一种未来努力,按其路径使用互联网和移动通信技术的算法设计一个安全系统。散射信息技术在对于许多基于隐写术的报纸使用的时候是非常有用的。隐蔽通信和隐写术的发展会增加更多的鲁棒数字水印的研究,能够使图像幸免于处理和攻击。我们希望在未来可以有一些商业化和有效的方案。在不久的将来,隐写技术最重要的应用可能会在于数字水印领域。内容提供商急于保护自己的版权作品反对非法分销和数字水印提供一种跟踪这些材料的主人的方式。将来我们可以在政府、软件公司、侦探机构等使用本文。涉及到相同的步骤来嵌入信息,发送给特定的用户。